How to Spot a Phishing Email
Antivirus Software Isn’t 100% Effective
You probably already know that installing an antivirus software program and keeping it up to date is a critical step in protecting your computer. This essential software uses virus signatures provided by software vendors to look for malware and stop it before it infects your PC (or Mac).

What you may not be aware of is that antivirus software does not offer total protection against malware infection. In fact, today’s malware authors will often use widely-available crypting services to ensure that their malware is completely undetectable by the majority of the antivirus software on the market.
Once they’ve made their malware “fully un-detectable,” the malware author is ready to deliver the AV-proof malware payload to their victims – often by way of a phishing email.
Beware of Phishing Emails and Social Engineering Attacks
What’s a “phishing email”? Phishing is a form of social engineering, a sophisticated threat involving the act of manipulating users into revealing confidential information or performing other actions detrimental to the user.
Phishing attacks use email or malicious websites to solicit personal information by posing as a trustworthy individual or organization. For example, an attacker may send email seemingly from a company executive or reputable financial institution that requests account information, often suggesting that there is a problem.
When an unsuspecting victim responds with the requested information, attackers can use that info to gain access to the accounts.
Phishing Email Examples
Take a look at the screenshot image below:
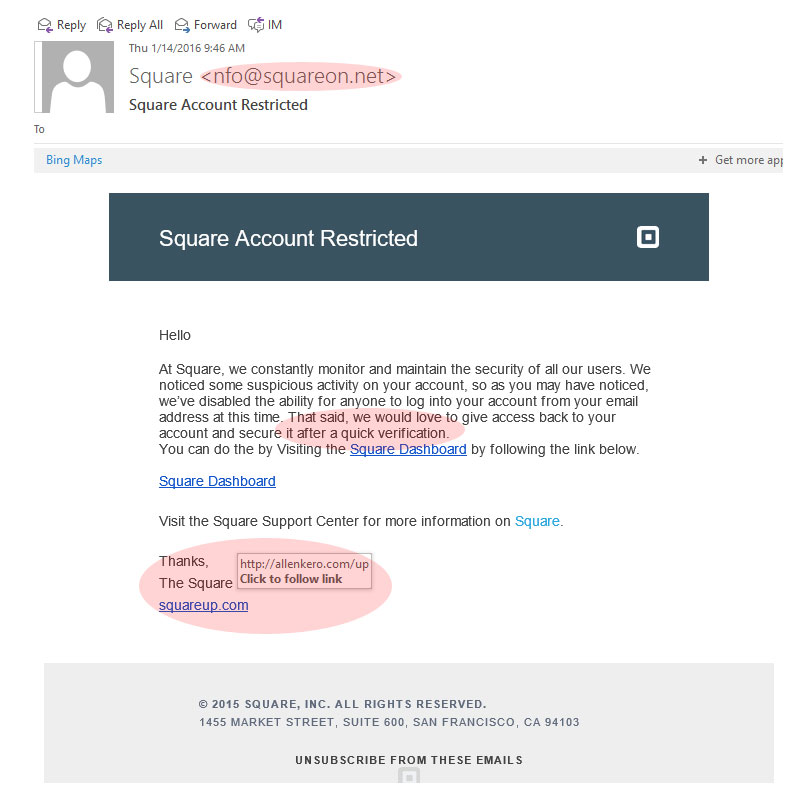
In this real-life example (which managed to bypass my email spam filtering only a few days ago), I received an email that appears to be from Square (a perfectly legitimate payment processing company that I happen to have an account with). The message is informing me of a problem (“Square Account Restricted”) and is urging me to click one of the links in the email for a “quick verification”.
In the screenshot image, I’ve highlighted several “red flags” I noticed in the message that clearly identify it as a phishing email. First, a legitimate company will NEVER send solicitations like this (unless you’ve initiated the request, like a password reset request, for example).
Second, the FROM address (“[email protected]”) is NOT an email/domain used by Square. Instead, it is faked or spoofed to look similar to a legit email address that would be used in an official communication from Square.
Third, by mousing over one of the links in the message I can see that the actual URL the link would take me to (“http://allenkero.com/up”) is NOT a legit domain name used by Square.
These red flags all point to a phishing email scam: the sender of this email was posing as a trusted organization (Square) and attempting to use that trust to get me to click on a potentially malicious URL link. (I did not click the link. Instead, I took a screenshot of the message and then promptly deleted it.)
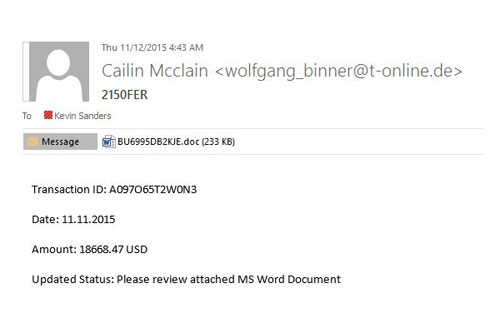
In another recent real-life example (see screenshot), I received an ambiguous message from “Cailin Mcclain” concerning a mysterious monetary transaction. The message is deliberately vague, inviting me to download and open an attached Microsoft Word Document that most likely contains a macro virus (I can’t say for sure, because I didn’t open it!)
Phishing Emails: Common Traits and Tactics
The scope of phishing attacks is constantly expanding, but frequent offenders tend to:
- Embed a link in an email that redirects the user to an unsecured website that requests sensitive information
- Install a Trojan via a malicious email attachment or ad which will allow the intruder to exploit loopholes and obtain sensitive information
- Spoof the sender address in an email to appear as a reputable source and request sensitive information
- Attempt to obtain company information over the phone by impersonating a known company vendor or IT department
Hackers and malware authors are very clever, and oftentimes it can be tough to tell the difference between a legitimate email and a phishing email. The bottom line is: don’t open email from unknown sources.
Be suspicious of unexpected emails that include attachments whether they are from a known source or not. When in doubt, delete the file and the attachment, and then empty your computer’s deleted items file. Don’t click on any URLs or links in the email if you are not sure of it’s origin.
Please watch out for phishing emails and other social engineering attacks. If you’re concerned about your cyber security and need help with anything discussed in this article, feel free to contact us.
