ABOVE: A photo of a screen showing what is apparently the skull splash page that appeared on Sony company computers when the attack started, posted by someone who said he was a former Sony employee who was sent the image by current Sony employees. The image was first posted on Reddit.
2013: The Biggest Retail Hack in History
By now most, readers will have heard about the massive data security breach that occurred in December 2013 that affected Target retail stores throughout the country. The biggest retail hack in U.S. history was designed to steal every credit card used at the company’s 1,797 U.S. stores, and largely succeeded in doing so, through a exploit involving one of Target’s third-party vendors.

Despite Target’s efforts to contain the breach, over 40 million credit card numbers were stolen and sent to servers in Russia, where cyber criminals sold them on the black market. Reports on the incident point out that although the security breach was in fact initially detected, corporate managers failed to take early action to contain it. Since then, the company has spent $61 million overhauling it’s security, C-level executives have resigned, and the company has suffered irreparable damage to consumer confidence.
2014: The Biggest Corporate Hack in History
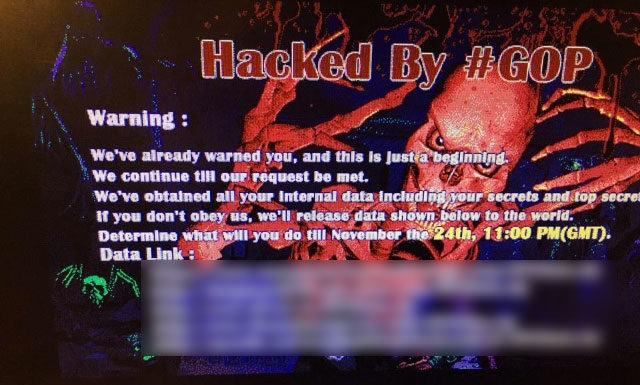
On November 24, 2014, Sony Pictures Entertainment was the victim of a brazen cyber attack by a powerful, sophisticated group of “hacktivists”, in the biggest, most widely-reported corporate hack in history.

The attackers stole massive quantities (around 100 TB) of files and “personally identifiable information” including employee social security numbers, usernames/passwords, and other sensitive data, which has been leaked on to the Internet for anyone to see.
Information Security Review – Home Users
Information security is becoming more and more important as our lives become increasingly digitized. For the average home user, the threat of a massive state-sponsored cyber attack directed at their small home network is very slim. However, there are some basic steps that every home user should take to maximize security:
- Passwords – Set secure passwords and don’t share them with anyone. Avoid using common words, phrases, or personal information and update regularly.
- Updates – Keep your operating system, browser, anti-virus and other critical software up to date. Security updates and patches are available for free from major companies.
- Authenticate – Verify the authenticity of requests from companies or individuals by contacting them directly. If you are being asked to provide personal information via email, you can independently contact the company directly to verify this request.
- Web Surfing – Pay close attention to website URLs. Pay attention to the URLs of websites you visit. Malicious websites sometimes use a variation in common spelling or a different domain (for example, .com instead of .net) to deceive unsuspecting computer users.
(Cybersecurity tips are listed courtesy of the Department of Homeland Security)
Information Security Review – Business Users
Businesses have special needs that go above and beyond securing passwords and doing OS updates.
When consumers open an account with your business, or register to receive information or purchase a product from your business, it’s very likely that they entrust their personal information to you as part of the process.
If their information is compromised, the consequences can be far – reaching: consumers can be at risk of identity theft, or they can become less willing – or even unwilling – to continue to do business with you.
These days, it’s just common sense that any business that collects personal information from consumers also would have a security plan to protect the confidentiality and integrity of the information. For financial institutions, it’s an imperative: The Gramm-Leach-Bliley Act and the Safeguards Rule, enforced by the Federal Trade Commission, require financial institutions to have a security plan for just that purpose.
The threats to the security of your information are varied – from computer hackers to disgruntled employees to simple carelessness. While protecting computer systems is an important aspect of information security, it is only part of the process. Sound security for businesses means regular risk assessment, effective coordination and oversight, and prompt response to new developments. Basic steps in information security planning include:
- Identify Risks – Identifying internal and external risks to the security, confidentiality and integrity of your customers’ personal information
- Safegaurds – Designing and implementing safeguards to control the risks
- Monitoring and Maintenance – Periodically monitoring and testing the safeguards to be sure they are working effectively
- Adapt and Adjust – Adjusting your security plan according to the results of testing, changes in operations or other circumstances that might impact information security
- Third-Party Management – Overseeing the information handling practices of service providers and business partners who have access to the personal information. If you give another organization access to your records or computer network, you should make sure they have good security programs too.
When setting up a security program, your business should consider all the relevant areas of its operations, including employee management and training; information systems, including network and software design, and information processing, storage, transmission and disposal, and contingencies, including preventing, detecting and responding to a system failure.
Although the security planning process is universal, there’s no “one size fits all” security plan. Every business faces its own special risks. The administrative, technical, and physical safeguards that are appropriate really depend on the size and complexity of the business, the nature and scope of the business and the sensitivity of the consumer information it keeps.