The Dangers of Remote Work
People who work from home are a favorite target for hackers, because the typical work from home (WFH) computer setup is less secure than a professionally-installed business computer inside of a protected company network/firewall.
As a result, hackers tend to view remote workers as relatively easy pickings: and frequently target them as a way to infiltrate company data.
In fact, law enforcement authorities have cited a rise in cyber-attacks (such as the ongoing $42-million ransomware attack against a New York based celebrity law firm) since the coronavirus crisis shut down the economy and forced many employees to work from home, where internet connections may not be as secure as in a workplace, and where workers may not have access to a company-issued (and security-hardened) business laptop computer.

With the exception of larger businesses that have issued a fleet of business laptops to their remote workforce, adopted modern zero trust security models to protect company data, and implemented advanced identity & access management systems, a small business that is trying to get a newly-minted work-from-home crew to be productive AND secure faces a tremendous challenge.
The big question for small businesses (and their IT departments) is: how can we help ensure that remote workers are secure, and are not exposing our company’s data to unnecessary risk of hacking?
If you asked any network security professional that question, one of their first answers would likely be: “Enable MFA!”
What is Multi-Factor Authentication (MFA)? Why is it so effective against credential attacks?
Traditional usernames and passwords can be stolen (as we saw with a phishing attack against one of our clients recently), and they’ve become increasingly more vulnerable to credential attacks.
Multi-Factor Authentication (MFA) is a security system that verifies a user’s identity by requiring multiple credentials. Rather than just asking for a username and password, MFA requires other—additional—credentials, such as a code from the user’s smartphone, the answer to a security question, a fingerprint, or facial recognition.
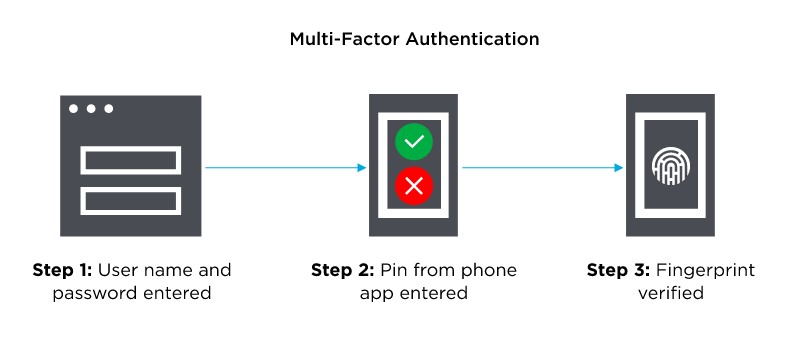
What makes MFA so effective against credential attacks? Imagine some hacker is trying to break into your account: if you have enabled MFA protection, the hacker must pass TWO tests to get in.
Even if they’ve already stolen your username/password (which can be trivial: see below) the hacker will fail the second authentication challenge – unless they’ve also managed to steal your phone and/or your fingerprints!
When going up against an MFA-hardened account, most hackers will decide not spend the significant additional time and effort required to break in, and will instead turn their attention to softer targets.
Your Pa$$word doesn’t matter
Speaking of passwords, we all know that they are a huge pain to manage. Even the would-be simple act of changing your password can be a complex task, due to the number of password rules that typically must be followed such as:
- MUST contain at least 8 characters
- MUST contain at least one uppercase/lowercase letter
- MUST contain at least one number and one special character (!?#$%&)
- MAY NOT contain first name, last name, email address mailbox or domain, company name or commonly used passwords
- MAY NOT match commonly used password character patterns
- … and so on
If you’re anything like the average computer user, you probably know that it’s nearly impossible to meet all the above requirements AND remember all of your passwords manually (this is why it’s we recommend protecting your accounts with a secure password manager, which does the work of creating, remembering, and retrieving passwords MUCH more effectively than a human can do with their brain and pen/paper).
However, even after you go through all of the trouble creating unique and complex passwords for all of your accounts, and you responsibly store them all in a secure password vault, guess what? Your password still doesn’t matter.
Despite all of your best effects, the bad guys will eventually steal your password, and they have multiple types of attacks and ways to do so.
Types of credential attacks (and how MFA blocks them)
In a blog post by Alex Weinert, the Director of Identity Security at Microsoft, he illustrates different types of credential attacks (i.e. attacks designed to steal passwords) and the importance of MFA in defending against them..
As you can see in the table below, the author points out that when it comes to composition and length, your password (mostly) doesn’t matter to hackers who are using these types of attacks:
| Attack | Also known as . . . | Frequency | Difficulty: Mechanism | User assists attacker by . . . | Does your password matter? |
| Credential Stuffing | Breach replay, list cleaning | Very high – 20+M accounts probed daily in MSFT ID systems | Very easy: Purchase creds gathered from breached sites with bad data at rest policies, test for matches on other systems. List cleaning tools are readily available. | Being human. Passwords are hard to think up. 62% of users admit reuse. | No – attacker has exact password. |
| Phishing | Man-in-the-middle, credential interception | Very high. 0.5% of all inbound mails. | Easy: Send emails that promise entertainment or threaten, and link user to doppelganger site for sign-in. Capture creds. Use Modlishka or similar tools to make this very easy. | Being human. People are curious or worried and ignore warning signs. | No – user gives the password to the attacker |
| Keystroke logging | Malware, sniffing | Low. | Medium: Malware records and transmits usernames and passwords entered, but usually everything else too, so attackers have to parse things. | Clicking links, running as administrator, not scanning for malware. | No – malware intercepts exactly what is typed. |
| Local discovery | Dumpster diving, physical recon, network scanning. | Low. | Difficult: Search user’s office or journal for written passwords. Scan network for open shares. Scan for creds in code or maintenance scripts. | Writing passwords down (driven by complexity or lack of SSO); using passwords for non-attended accounts | No – exact password discovered. |
| Extortion | Blackmail, Insider threat | Very low. Cool in movies though. | Difficult: Threaten to harm or embarrass human account holder if credentials aren’t provided. | Being human. | No – exact password disclosed |
| Password spray | Guessing, hammering, low-and-slow | Very high – accounts for at least 16% of attacks. Sometimes 100s of thousands broken per day. Millions probed daily. | Trivial: Use easily acquired user lists, attempt the same password over a very large number of usernames. Regulate speed and distributed across many IPs to avoid detection. Tools are readily and cheaply available. See below. | Being human. Using common passwords such as qwerty123 or Summer2018! | No, unless it is in the handful of top passwords attackers are trying. |
| Brute force | Database extraction, cracking | Very low. | Varies: Penetrate network to extract files. Can be easy if target organization is weakly defended (e.g. password only admin accounts), more difficult if appropriate defenses of database, including physical and operation security, are in place. Perform hash cracking on password. Difficulty varies with encryption used. See below. | None. | No, unless you are using an unusable password (and therefore, a password manager) or a really creative passphrase. See below. |
According to Weinert:
Only in password spray and cracking attacks does the password have any bearing at all on the attack vector. Go turn on MFA if you haven’t.
[…]
Your password doesn’t matter, but MFA does! Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.
In other words, your password doesn’t matter because 1) complex & unique passwords can be stolen, and 2) if you have MFA enabled, 99.9% of attacks can be blocked even if your password has been stolen.
So why haven’t you enabled MFA on all of your sensitive accounts yet?
Enable MFA – Now
It’s an IT security best practice to enable MFA whenever possible, and to add this effective security layer to help protect your personal and business accounts from credential attacks (which are very common).

Don’t wait for your account to be compromised or your passwords to be stolen: go enable MFA for all of your important personal and business accounts right now. If your employer’s IT department must approve enabling MFA, ask them to do so (and if the IT department does not offer an MFA solution, ask them why they don’t).
The good news is that most major tech companies such as Facebook, Google, Microsoft, and Apple have built-in MFA solutions available for both their consumer and business product lines. To enable MFA, look in your account’s privacy or security settings (the exact steps are different, depending on the type of account).
MFA is especially important for remote workers, who are normally connecting to vulnerable home Wi-Fi networks and using un-patched personal laptops, because they’re more at risk of being the victim of a credential attack.
More information
If you need help with enabling MFA or have questions about computer security in general, feel free to contact us.
