Why should you care about ransomware?
The unfortunate truth is that ransomware attacks are becoming more and more prevalent in our everyday lives, with many people and businesses falling victim to these increasingly sophisticated and destructive cyber crimes.
According to NPR.ORG, the United States suffered 65,000 ransomware attacks last year – or seven attacks per hour. And it will probably get worse, according to most experts.
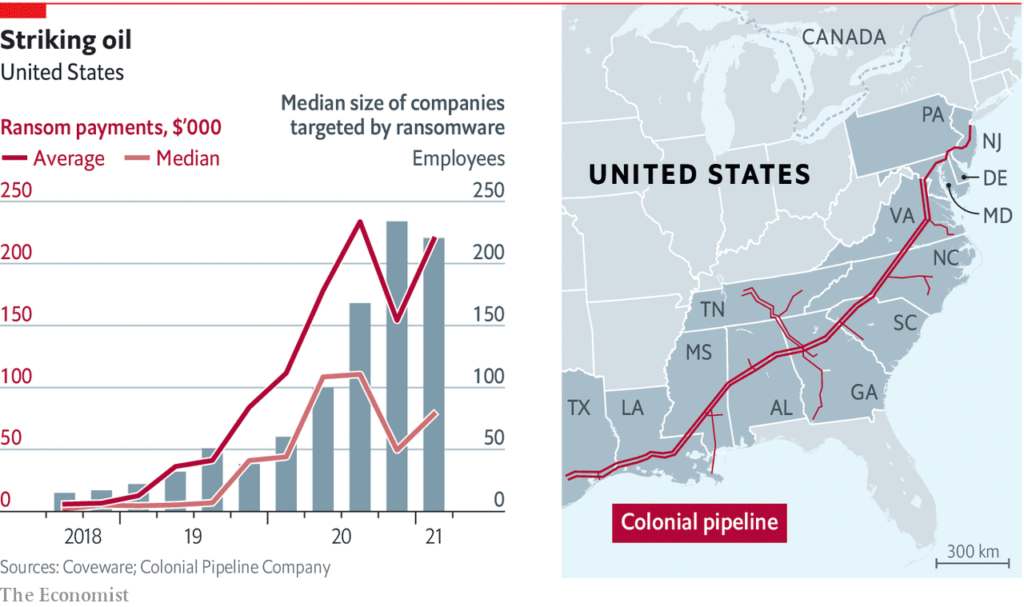
Last month, cyberthugs famously launched a successful ransomware attack against Colonial Pipeline which shut down half the East Coast’s fuel supply and netted the criminals over $4.4 million in Bitcoin after the CEO decided to pay the ransom to unlock the company’s IT systems and resume operations.
Think your business is “too small to hack”?
Ransomware may be big business for digital outlaws, but it affects victims of all sizes – particularly small businesses. In fact, the Homeland Security Secretary Alejandro Mayorkas recently warned that ransomware attacks against small businesses comprise “approximately one-half to three-quarters of the victims” and that overall attacks have been up almost 300% this year.
What can be done about this tidal wave of cyber terror and extortion?
In this blog post, we’ll lay out some basic ransomware protection and recovery measures that all businesses – big or small – should be implementing.
How to protect against ransomware
1. User Security Awareness and Training
Users – everyday employees and staff members – are your first line of defense against online threats. Protecting and educating your people about cyber security should be a high priority within your organization.
User security awareness and training is #1 on this list for good reason. Hackers prefer to target users with phishing attacks and malicious links in emails, because it’s often easier to trick people into downloading malware – which can lead to serious security problems – than it is to try and break a company’s technical defenses.

Humans, as it turns out, are usually the weakest link in a company’s security.
This is why it’s absolutely critical to train your users how to identify potentially malicious links in emails – as emails are the preferred vector of attack – in addition to implementing a security awareness training program and promoting a culture of security within your organization.
2. Least Privilege Access (no local Admin)
As a security best practice, your users should NOT be logged in as administrators on their computers in the course of their data-to-day work.
The reason for this is simple. If a user is logged in as an admin, and they get infected with malware (such as ransomware), then the malicious software will be able to execute with elevated admin privileges – and run rampant through your network. The malware can then easily spread to other parts of your business including other computers and servers.
Take the basic step of ensuring that your users are logged in with standard accounts (not administrator accounts) on their computers – it’s a relatively easy to implement and effective layer of defense.
3. Operating System Updates
In addition to going after users through social engineering scams, phishing, and other confidence tricks, many cyber criminals also launch attacks designed to target technical vulnerabilities in software, often through zero-day exploits of unpatched systems.
This method of attack continues to be an effective tactic for hackers because a surprising number of organizations fail to keep their systems updated in a timely manner, and will often postpone critical operating system updates – until it’s too late.
Don’t skip these critical updates! Though it may be slightly inconvenient to occasionally have to restart your computers (and servers) to complete OS updates, these software patches are essential for protecting your systems against ransomware – and the updates usually add new features and make your systems more reliable and compatible, too.
4. Anti-Virus Software
Anti-virus software, while not as effective as it once was due to the advanced capability of modern malware to evade detection, is still an important layer of defense for businesses and individuals alike.

Make sure that a professional AV software solution is installed on all of your computers, and make sure that the software is up-to-date.
5. Windows 10 Ransomware Protection (Built-in)
Did you know that Windows 10 has certain ransomware protection features that are built-in to the operating system?
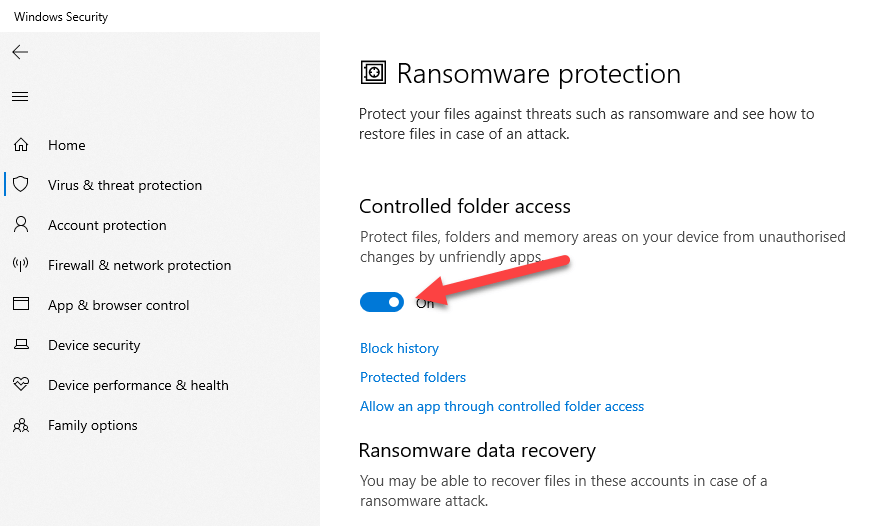
They’re not enabled by default, and require some configuration, but with controlled folder access and OneDrive you can implement additional protection against ransomware on your PC.
(NOTE: before implementing this on your PC, read Microsoft’s documentation first to avoid any adverse effects on your files.)
6. Backups
If all else fails, a functioning data backup and recovery system is your last line of defense against ransomware – and other threats to your data like common hardware/software failures, for that matter.

It’s extremely important that you maintain up-to-date copies of ALL your data – everything from files stored on local servers to user data (email, documents, etc) stored on both local computers AND cloud accounts.
Additionally, if you have one or more local servers in your office that host critical business data, you should have air-gapped backup systems as well.
What does “air-gapped” mean? If your “backup” is just a USB drive plugged into your server, or a NAS storage device that’s 100% visible on your network through an SMB share, then guess what? Modern ransomware is advanced enough to be able to discover those poorly-protected backup devices and infect the backup files too – rendering the backups completely useless.
Invest in a robust backup system, and make sure it’s as “ransomware-proof” as possible by air-gapping the system and syncing up with cloud copies of the data, too.
7. Test Your Ransomware Protection
So you’ve implemented the steps above to protect your organization from ransomware attacks and data loss – well done!
But how do you know that you’re really protected? How can you test your ransomware protection measures? Here are a few ways:
- Send your user simulated phishing emails (you can use a service like KnowB4) to identify which users need more training.
- Enroll your users in security awareness training (KnowB4) and measure their progress.
- Audit user access controls (Active Directory, Azure AD) to make sure users don’t have access to critical files/folders or local admin privileges.
- Check all software updates regularly, and have a patching/maintenance plan in place.
- Run a ransomware simulator (KnowBe4, CryptoStopper) and test the results.
- Test your backups to make sure that they work! Quarterly or even monthly testing is recommended, and always be sure that you get an alert if for some reason a backup fails to run.
Be sure to test your protection measures regularly, to ensure that they are effective and working as designed.
Ransomware attack data recovery (worst case scenario)
If you find yourself in a worse case scenario (like what happened to one of our clients a few years back), and a ransomware attack has completely locked down all of your business files and paralyzed your operations, your options are unfortunately very limited.
8. Try to crack the encryption
You can attempt to decrypt the data yourself, without relying on a special tool or key provided by your attacker (good luck).
The main problem with this option is that it’s nearly impossible to crack modern encryption standards (AES-256 combined with RSA-2048) without a key – even the most powerful supercomputers in the world working night and day would take billions or trillions of years to complete the task.
If you’re “lucky” enough to be infected by an older or weaker ransomware variant – and you can identify the exact variant – it may be possible to find a security company that has already developed a decryption tool for your particular case, and pay them a small fee (usually much less than the ransom amount) to decrypt your data for you.
9. Restore from backup
Restoring from backup is usually the preferred recovery option because it doesn’t involve paying the hackers money, and thus doesn’t perpetuate the criminal ransomware “business model”.
However, successfully recovering from a ransomware attack by restoring from backups may be easier said than done.

Assuming your backup systems actually work (you’ve been testing them on a regular basis, right?) initiating a full-blown system data restore can be a complex and time-consuming method for recovering from a ransomware attack.
Depending on the amount of data that needs to be recovered, a full backup restore can take time – a long time. The difference between restoring a single server with 100 GB of data, versus recovering multiple servers in different locations with 100 TB of data, can take anywhere from a single day to several weeks.
A business that has suffered a large-scale ransomware attack often can’t afford to be down for such a long time. This is precisely the reason why many CEOs make the decision to pay the ransom – it’s usually much faster than restoring from backup.
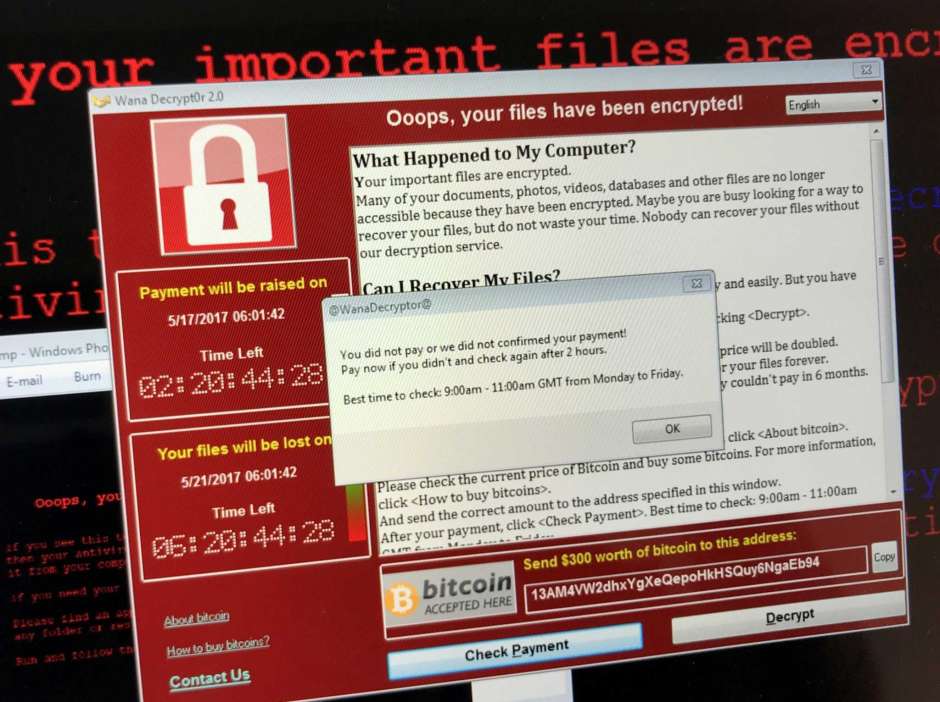
10. Pay the ransom (and hope the decryptor works)
“We can’t wait to restore from backup (or our backups don’t work). Let’s pay the ransom for the hackers unlock our data.”
In reality, many times the fastest way to recover from a serious ransomware infection is to give they cyber criminals what they want – money.
A business that’s been hit with ransomware is given the option to send the criminals a certain amount of cryptocurrency (ie Bitcoin) in exchange for a special decryption tool, which can then be used to unlock their files.
The hackers will normally provide helpful instructions for obtaining Bitcoin, transferring the payment, and running the decryption tool (how thoughtful of them!)
In a fraction of the time it would take to restore from backup, the locked files can simply be decrypted using the key provided by the criminals – and then it’s back to business as usual.
Many businesses make the calculation that it’s more cost-effective to pay a ransom and get back to operations as quickly as possible. Cybercriminals know this – and it’s the primary reason why ransomware has become a multi-billion dollar business and is getting more and more sophisticated (and lucrative) every day.
Problems with payment
However, paying the ransom is not 100% guaranteed to work – either because of flaws in the hacker’s decryption tool, and/or the possibility of the criminals simply taking the money and running off with it.
Even if a company does decide to pay up, without a thorough security review and remediation effort to ensure that no trace of the malware remains hidden in the company’s IT systems, there’s still no guarantee that the hackers (or one of their partners in crime) won’t simply re-infect the same company and demand another ransomware payment.
Paying a ransom may also very well result in a company running afoul of the law.
There is currently a heated debate amongst cybersecurity professionals and government officials on whether or not to ban ransomware payments and make them illegal. Some people believe you can’t solve the problem without banning payments. On the other hand, there are victims who are really impacted by ransomware and their viability as businesses would be existentially threatened if payments were banned.
Conclusion
In summary, if you’ve already been infected with ransomware, you really don’t have any good options.
The best course of action is to invest in the ransomware protection and recovery steps outlined above, and protect yourself and your company against being infected in the first place.
Of course, if you have any questions feel free to contact me for help.
