The Lone Star State ransomware attack — which resulted in portions of 22 town and county networks being locked by encrypting ransomware last month — was perpetrated by hackers who successfully targeted a single managed IT service provider (MSP) based in Texas.
The attack caused serious damage to the organizations affected, spawned multiple lawsuits and insurance claims, and inflicted irreparable harm to the MSP’s reputation and business.
Why are hackers targeting MSPs?
The simple answer is because MSPs usually have remote administrative access to all of their customers’ computers — with total “endpoint” counts numbering in the hundreds or thousands of machines — and are thus high value targets.

If a hacker can successfully exploit weaknesses in an MSP’s remote monitoring & management (RMM) software, and/or take advantage of an MSP’s lax internal security practices, it’s possible to infect hundreds or perhaps thousands of the MSP’s customer machines in a single attack.
Can’t the MSP just restore from backup?
If a single customer suffers from a large data loss (such as a loss caused by ransomware), an MSP’s standard practice is to begin restoring the customer’s data from a backup, which is oftentimes a labor-intensive process but still fairly straightforward.
If multiple customers go down at the same time (due to a ransomware attack), the amount of labor needed to restore all customer systems can quickly overwhelm an MSP’s resources.
For this reason, MSPs sometimes prefer to pay the ransom. Hackers know this and have leverage in ransom negotiations because the MSP — usually a small business itself — can’t handle the volume of work for dozens of affected clients who simultaneously demand attention.
How much does a ransom payment cost?
Ransomware is big business. This info graphic shows how profitable ransomware can be for hackers:
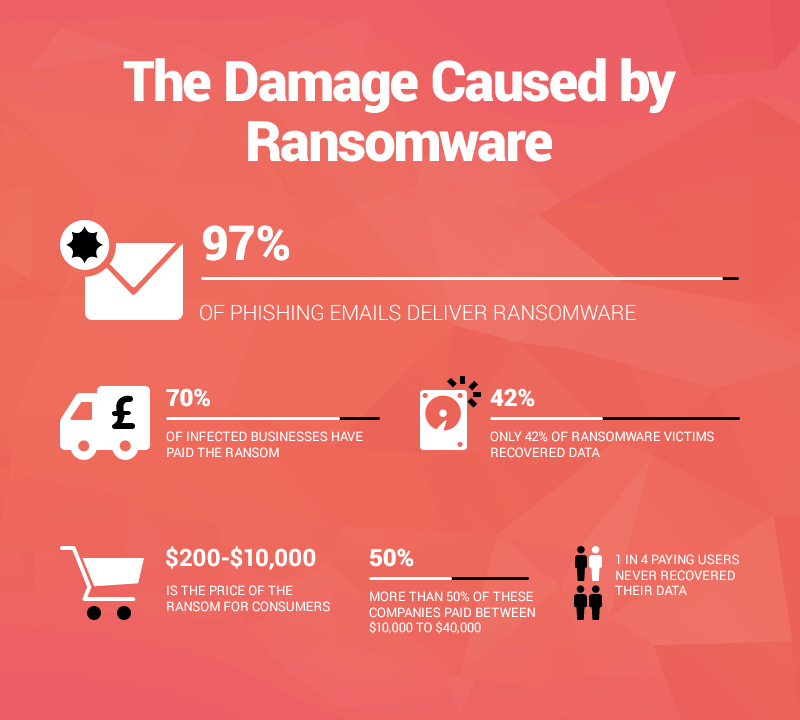
Instead of going after consumers, organized hacker groups are increasingly targeting businesses (and their outsourced IT providers) because they are more likely to receive a large ransom payment.
How do we know if our MSP is protecting our company data?
“Hacking an MSP and then encrypting all their clients is hugely profitable. There is such a huge return on investment … its low hanging fruit,” said Fabian Wosar, a London-based cyber-security expert.
“MSPs never had to deal with it, so in a way they got away with a lot of shady practices, and bad cyber-hygiene. Either they were lazy or they didn’t know any better, you had a lot of them who are vulnerable to this type of attack.”
The short answer is: it’s hard to know for sure.
“Who is vetting these [MSP] providers? Who is asking if they’re doing things right?” said cyber-security guru Brian Krebs. “On a lot of occasions, they’re not. Or they haven’t updated their security procedures and requirements for years.”
In the case of the Texas ransomware attack, the owner of MSP which was hacked said he had outsourced the IT work on the victimized customers to a white-box, third party IT provider who he believes left login credentials on a compromised machine.
The owner of that MSP also said they were not enforcing two-factor authentication (2FA), which made it easier for hackers to compromise administrative accounts using stolen passwords.
More information
If you have any questions about how to secure your business from cyber threats such as ransomware, please contact us today.