Encrypting Ransomware — a type of malicious software (malware) that encrypts the victim’s files and holds them hostage until the victim pays a ransom in Bitcoin — has emerged as a potent and increasingly common threat online.
What is Encrypting Ransomware?
If you’ve already heard of ransomware, it’s probably because mainstream news outlets like BBC, New York Times, and Wall Street Journal have been reporting on the threat in the past year.
In particular, high profile cases of successful attacks against U.S. hospitals (including at least one L.A hospital) have drawn significant attention.
Ransomware is on the rise, and companies are feeling the pressure – with almost 40 percent of businesses experiencing a ransomware attack last year alone, according to research from computer security firm Malwarebytes.
What makes this type of malware the preferred choice for criminal hackers victimizing people for personal gain? Judging from the number of reported cases of victims paying the ransom, ransomware is quite profitable:
Cyberextortion and blackmail are hardly new things, but cybercriminals have just about perfected their techniques of extracting money from the masses through the use of ransomware. Businesses and everyday folk all rely on data that rests on their PCs, mobile devices and web servers more and more each day. Maybe not enough to reliably back it up, but certainly enough to go into a blind panic when criminals encrypt their data and dangle the prospect of a decryption key for a fee. The fear is palpable and pervasive enough for the crooks to make a killing off the practice.
Security researchers agree that ransomware has taken over the cybercriminal world in the last few years – and there’s no end in sight.
Ransomware criminals are targeting individuals and small businesses
At this point, you may be thinking “Hey, stop fear-mongering over some kind of new computer virus that will likely never affect me. This kind of stuff only affects big corporations, and besides, I back up my files to ‘the cloud’!”
My intention with this post isn’t to scare the reader. Actually, the reason I’m writing this is because of an experience with a client that scared me recently.
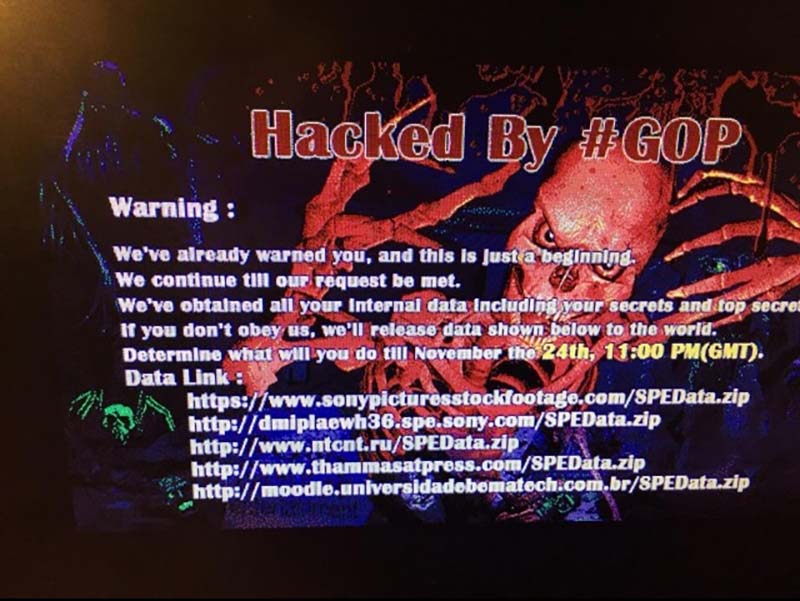
The now infamous “splash page” of the 2014 Sony hack. (Tip: DON’T VISIT the URLs listed in the image)
I’ve cleaned up my fair share of computers (mostly PCs, and some Macs too) infected with all kinds of garden-variety malware including viruses, trojans, spyware, adware, and rootkits over the years. I’ve stayed current on news of the latest data breaches, hacks, and security threats, but it wasn’t until last month that I’d even seen a ransomware attack “in the wild.”
The call came from a small business client (a survey company with under 25 users) reporting file access problems. They described what had happened: their bookkeeper suddenly couldn’t open any documents, and soon after that other users were complaining that they couldn’t access their files.
I knew that it was an encrypting ransomware attack when the client told me that the bookkeeper’s PC was displaying a message with instructions for acquiring Bitcoins to pay for a “decryption key.” Even worse, the client’s main file server appeared to be infected – and they didn’t know if they had working backups of their data.
This was not good. I won’t go into all of the details about what happened in this blog post, but suffice it to say that the survey company experienced several days of downtime, lost data, lost productivity, and lost revenue.
What really struck me was the absolute chaos inflicted by the ransomware attack. The victimized company was completely paralyzed: the ransomware not only infected/encrypted the files on the bookkeeper’s PC, but had also spread through the network shared folders and began encrypting documents on the company’s main file server (fortunately, one of the company’s database programmers recognized the attack and had pulled the power cord from the file server mid-infection, limiting the damage).
Even so, the company’s cloud backup took days to download via their slow Internet connection. Furthermore, the company’s lack of IT documentation combined with an inadequate backup/disaster recovery (BDR) solution made the attack extremely difficult to recover from.
Ransomware is spreading
The authors of ransomware instill fear and panic into their victims, causing them to click on a link or pay a ransom, and users systems can become infected with additional malware. A new study shows that the total number of new malware samples (led by encrypting ransomware variants) has skyrocketed in recent years:
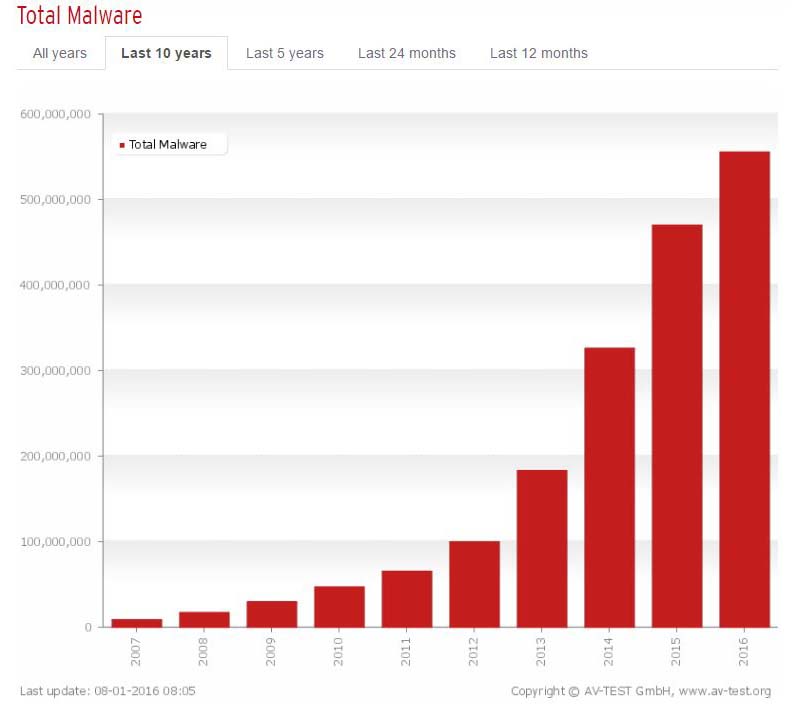
Source: AV-TEST.ORG
Because people report only a fraction of ransomware attacks to federal authorities, it’s hard to say exactly how big the problem is. By most accounts, however, the problem is on the rise.
Ransomware is very effective
According to US-CERT.GOV, ransomware is often spread through phishing emails that contain malicious attachments or through “drive-by downloading.” Drive-by downloading occurs when a user unknowingly visits an infected website and then malware is downloaded and installed without the user’s knowledge.
Ransomware not only targets home users; businesses can also become infected with ransomware, leading to negative consequences, including:
- Temporary or permanent loss of sensitive or proprietary information
- Disruption to regular operations
- Financial losses incurred to restore systems and files
- Potential harm to an organization’s reputation
Paying the ransom does not guarantee the encrypted files will be released; it only guarantees that the malicious actors receive the victim’s money, and in some cases, their banking information. In addition, decrypting files does not mean the malware infection itself has been removed.
Ransomware is difficult to defend against
Infections can be devastating to an individual or organization, and recovery can be a difficult process that may require the services of a reputable data recovery specialist.
US-CERT recommends that users and administrators adopt a “multi layer” approach to guarding against ransomware, and take the following preventive measures to protect their computer networks from ransomware infection:
- Employ a data backup and recovery plan for all critical information. Perform and test regular backups to limit the impact of data or system loss and to expedite the recovery process. Note that network-connected backups can also be affected by ransomware; critical backups should be isolated from the network for optimum protection.
- Use application whitelisting to help prevent malicious software and unapproved programs from running. Application whitelisting is one of the best security strategies as it allows only specified programs to run, while blocking all others, including malicious software.
- Keep your operating system and software up-to-date with the latest patches. Vulnerable applications and operating systems are the target of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker.
- Maintain up-to-date anti-virus software, and scan all software downloaded from the internet prior to executing.
- Restrict users’ ability (permissions) to install and run unwanted software applications, and apply the principle of “Least Privilege” to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through the network.
- Avoid enabling macros from email attachments. If a user opens the attachment and enables macros, embedded code will execute the malware on the machine. For enterprises or organizations, it may be best to block email messages with attachments from suspicious sources. For information on safely handling email attachments, see Recognizing and Avoiding Email Scams. Follow safe practices when browsing the Web. See Good Security Habits and Safeguarding Your Data for additional details.
- Do not follow unsolicited Web links in emails. Refer to the US-CERT Security Tip on Avoiding Social Engineering and Phishing Attacks or the Security Publication on Ransomware for more information.
Individuals or organizations are discouraged from paying the ransom, as this does not guarantee files will be released. Report instances of fraud to the FBI at the Internet Crime Complaint Center.
Ransomware is big business
In recent years, cyber criminals have greatly enhanced the underground economy powering the business of ransomware. Today, any script kiddie can purchase a pre-built “ransomware as a service” (RaaS) kit on the dark web and start their own online extortion business with relative ease.
Armed with the computing power of the cloud, identity-hiding technologies such as TOR, and untraceable crypto-currencies such as Bitcoin, an aspiring criminal hacker can successfully target and infect large numbers of victims with any number of encrypting ransomware variants. He can begin ransoming stolen data for real cash almost immediately with a good kit and a cleverly-worded spoofed email message.
Some of the more enterprising criminal hackers who purchase the “enterprise” tier kits from RaaS distributors can even gain access to a full “ransomware help desk”, staffed with “tech support” reps who cheerfully guide victims through the somewhat technical process of purchasing and transferring Bitcoins to the criminal hacker in exchange for decryption keys, which the victims desperately need in order to unlock their files and data.
The U.S. ransomware market has exploded from a $400,000 annual haul in 2012 to nearly $18 million in 2015. Criminal hackers control huge botnets worldwide that send out legitimate-looking malicious emails capable of penetrating most networks, evading traditional anti-virus protection, and fooling even the most carefully trained users.
And they’re only getting better at it.
