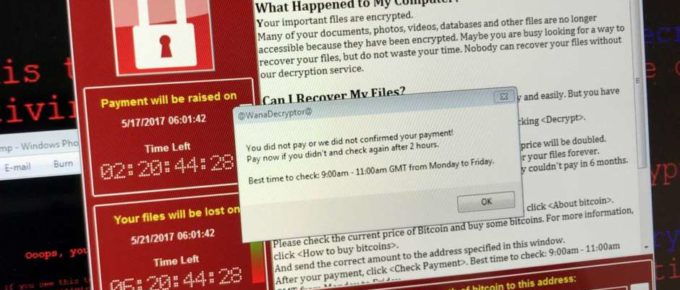
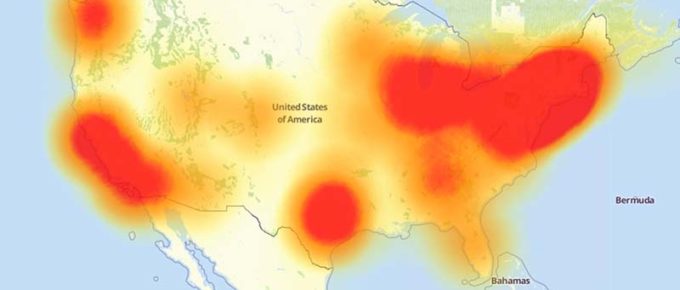
The Lone Star State ransomware attack — which resulted in portions of 22 town and county networks being locked by encrypting ransomware last month — was perpetrated by hackers who successfully …
Continue Reading about Hackers are Targeting MSPs (and their Customers) with Ransomware →