
What is a phishing attack?
A phishing attack, or a phishing scam, is when a criminal sends an email pretending to be someone (ex. the CEO of your organization) or something he’s not (ex. Microsoft), in order to extract sensitive information out of the target.
Recently, one of our client’s end users (an employee) was the target of a phishing attack that resulted in a security incident.
Here’s what happened (client and user names protected for privacy):
How the attack started
The attack started when the employee – let’s call him “Steve” – received an email from his colleague “Pam”.
Steve and Pam had corresponded via email many times before. The email that Steve saw in his Outlook desktop app looked similar to this example:
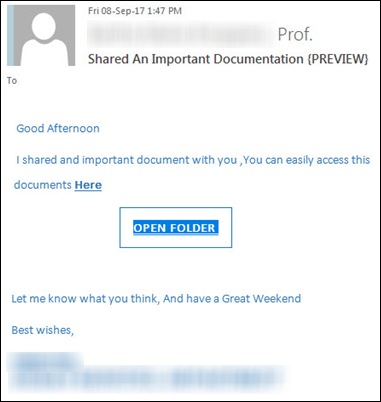
Pam appeared to be asking Steve to open an “important document” that she had shared via a hyperlink – but she was noticeabley short on any other detail.
Steve later recalled thinking this was a bit odd, because he wasn’t expecting to receive any documents from Pam.
But he knew and trusted Pam, so he clicked the link.
A link to a normal-looking website..?
Clicking on the link opened up a website in Steve’s default web browser application – in this case Google Chrome.
The website looked similar to this:

Steve recognized the “OneDrive” logo, because his company uses the popular Microsoft Office 365 service and he personally uses the OneDrive app to share files with colleagues on a daily basis.
The website, which looked like the real Microsoft website, instructed Steve to download a file – and invited him to enter his company email address and submit his company email password.
Something’s wrong
Steve obliged: he entered his email address and password, and clicked “Download File”…
… and then got an error message. The error said something like this:
Invalid login credentials. Please enter the correct email address and/or password.
So he tried again, but got the same error. This was strange, because he knew for certain that he was entering the correct password (which he had retrieved from his password management software)
At this point, he realized something was wrong, so he contacted his IT support team (us) for help and submitted a help request.
Alerting IT, determining the scope of the problem
Steve’s initial help request was to resolve “some outlook issues”, saying he “cannot log in” and was “trying to open a link to One Drive shared documents”.
At this point, we were treating this as a “I need a password reset” type of request, as we have helped end users with this common request many times before.
However, when Steve informed us that he’d spoken with Pam – and that she claimed she never sent him that email and suspected she had been “hacked” – we knew very quickly this was a potentially more serious problem and escalated the request to Urgent priority.
Change your password – now!
A quick phone call with Steve was enough to know we were dealing with a phishing attack.
Even worse, it appeared the attacker’s fake Microsoft website had successfully harvested Steve’s company login credentials – and resulted in a password compromise.

This was suddenly a potentially very serious security incident. We immediately took the following remediation steps:
- Reset the user’s compromised password
- Checked other accounts that were re-using the same compromised password, and reset those passwords too (this incident illustrates why it’s a bad idea to re-use passwords)
- Checked Outlook for suspicious activity (new forwarding rules, recently sent messages, changes to account settings, etc.)
- Informed the sender (Pam) of the malicious email sent from her account
Fortunately, the attack was detected and mitigated relatively quickly (thanks in no small part to Steve, who correctly identified that he had been targeted, and then immediately raised the alarm. Pam should be credited, too, for helping to detect the attack) and no permanent damage was done.
How to spot a malicious website
The security incident highlighted that the most critical line of defense against cyber attacks is user security awareness.
Remember the fake Microsoft website? Steve could have looked at the URL of the hyperlink Pam sent him, and noticed that it did NOT point to a trusted website such as https://microsoft.com but to an unknown page instead:
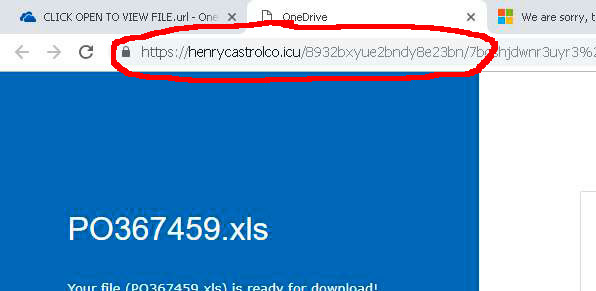
By examining the URL of a link – especially a link received unexpectedly from an unknown sender – Steve could have identified the malicious website and avoided the attack.
It’s worth noting that if Steve had two-factor authentication or 2FA enabled for his account, any attacker trying to log in with the stolen password would have been effectively stopped.
(We strongly recommended that the company set up mandatory 2FA enforcement for all users shortly after this attack occurred.)
Users are the first line of defense
Silverleaf invests significant resources helping our clients with their company’s cyber security: everything from monitoring updates, backups, AV definitions, firewall logs, user access controls – the list goes on.
However, even with these multiple layers of technical defense in place, a company can still fall victim to a major attack because of weak human defenses – for example, a phishing attack that succeeds due to insufficient user security training and awareness.
Therefore, a significant part of the responsibility (and burden) of a company’s overall cyber security must lie with the everyday end-users.
Users should be aware of common security threats, follow basic security best practices, and report suspicious activity to their IT department immediately.
More information
We hope this article has helpful, and we want all readers to be able to identify and prevent email-based phishing attacks (which are extremely common).
Here are some other posts you may find useful:
How to Spot a Phishing Email: Tips and Examples
4 Tips to Improve your Cyber Security
CASE STUDY: Encrypting Ransomware Hits Small Business
FTC Releases Cyber Resources for Small Businesses
BONUS SECURITY TIP: try to “mouse-over” (or “long tap/press” if you’re on a mobile device) to get a preview of where a URL link will take you, BEFORE you click or tap on it!
UPDATE: here’s a link to Microsoft’s guidance on Responding to a Compromised Email Account that has a very thorough remediation checklist
